IT Policy
This IT Policy can be used to ensure that your employees are aware of your expectations regarding workplace computer, internet, social media, internet and phone use and associated communication standards. This Policy also ensures that employees are aware that the Company owns the technology and has the right to monitor such use and content.
Last updated October 23, 2025
Suitable for Australia
Create & Customise Legal Templates Online
What is a it policy?
What is a it policy?
When should you use a it policy?
When should you use a it policy?
What should be in a it policy?
What should be in a it policy?
How to create a legal document
- check_circle
Access the Document Library
- check_circle
Select the template that matches your needs
- check_circle
Customise by adding or removing clauses with assistance from Lawpath AI
- check_circle
Personalise with your headers, footers, logos, or additional text
- check_circle
Store all documents securely in your account for easy access
Frequently asked questions
How does this policy protect my business?
keyboard_arrow_upDoes the policy cover remote and work-from-home arrangements?
keyboard_arrow_upWhat are the main limitations for employees under this policy?
keyboard_arrow_upCan the company monitor employee emails and internet usage?
keyboard_arrow_upWhat happens if an employee breaches the policy?
keyboard_arrow_upHow often should the policy be reviewed and updated?
keyboard_arrow_upWhat steps should I take after adopting this policy?
keyboard_arrow_upView Sample IT Policy
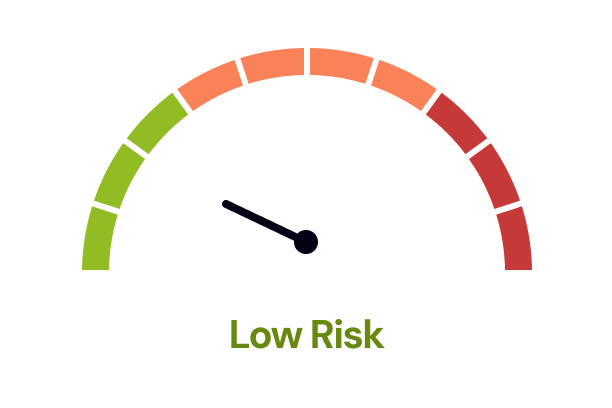
The Legal Risk Score of a IT Policy Template is Low
Our legal team have marked this document as low risk considering:
- There is a risk of privacy invasion as the document allows for extensive monitoring and recording of employees’ internet usage, email, and voice communications, potentially leading to discomfort or concerns about personal privacy.
- The document imposes strict limitations on the personal use of company IT resources, which could restrict employees' freedom to engage in personal activities during work, possibly affecting morale and satisfaction.
- The policy mandates that all data generated during business operations is owned by the Company, which may limit employees' control or rights over their own work outputs, potentially leading to intellectual property concerns.
Meet Our Users
Articles about IT Policy
Looking for more documents?
Privacy Policy
A Privacy Policy outlines how your business will use, store and collect your customers' information. A Privacy Policy is required by law in certain circumstances.
Loan Agreement
This Loan Agreement can be used by lender when offering a loan to a Borrower.
Non-Disclosure Agreement (Mutual)
A Non-Disclosure Agreement (Mutual) allows you and another party to share confidential information while legally forbidding either party from disclosing that information to any other person or entity.
Non-Disclosure Agreement (One Way)
A Non-Disclosure Agreement (One Way) allows you and another party to share confidential information while legally forbidding the other party from disclosing that information to any other person or entity.
Employment Agreement (Casual)
This Employment Agreement (Casual) is suitable for casual employees in any industry. This agreement is essential when hiring new casual employees for your business.
Business Sale Agreement
A Business Sale Agreement is used to clearly set out all relevant terms of the sale when selling or buying a business.
Contractor Agreement (Individual)
The Contractor Agreement (Individual) allows you to hire a contractor that is an individual (ie. not a company).
Shareholders Agreement
A Shareholders Agreement allows you to clarify the relationship between shareholders of your company.









